
Python is a general purpose programming language that is often applied in scripting roles. It is commonly defined as an object-oriented scripting language – a definition that blends support for OOP with an…
Read more
Designing the database is a key step, largely because changes to the database at a later date have far larger implications and potential complications than changing any other aspect of the site. Adding functionality through…
Read more
Python is one of those rare languages which can claim to be both simple and powerful. Python is an easy to learn, powerful programming language. It has efficient high-level data structures and a simple…
Read more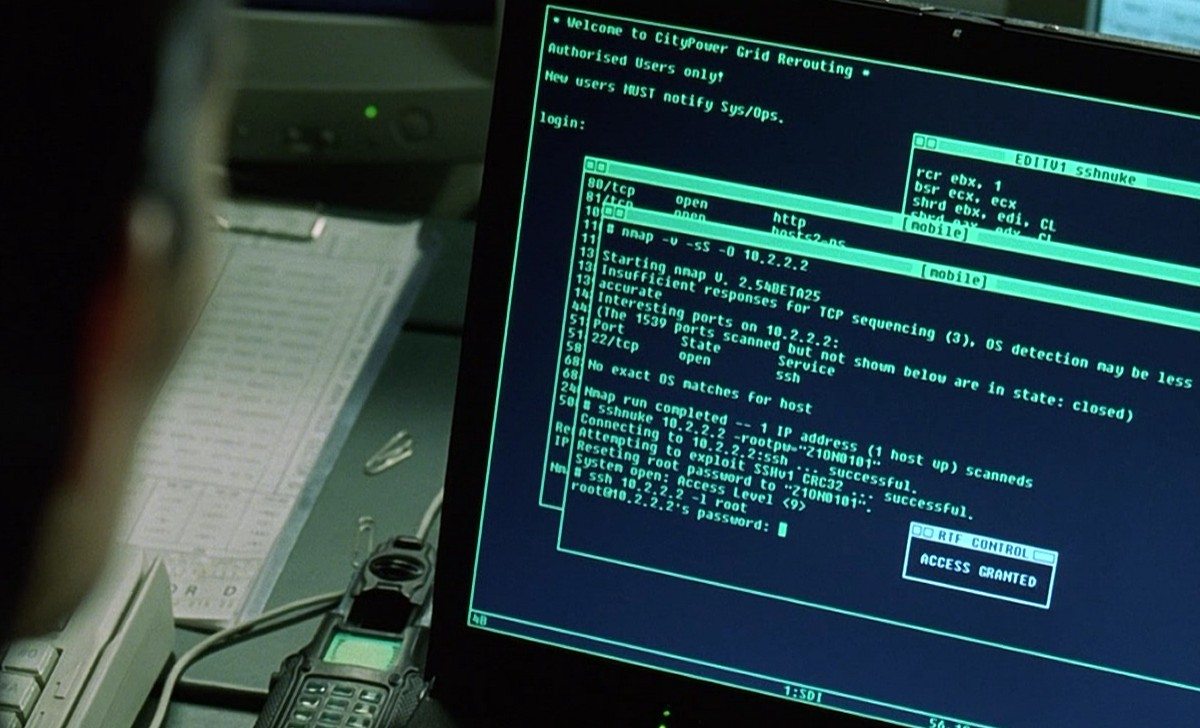
Nmap supports many scanning technologies, such as: UDP, TCP connect(), TCP SYN (half-open scan), ftp proxy (bounce attack), reverse flag, ICMP, FIN, ACK scan, Xmas Tree, SYN Scan and null scan. Nmap also…
Read more
Database A repository to store data. For example, a database might store all of the data associated with finance in a large company, information about your CD and DVD collection, or the records…
Read more
We have compiled a full list of Internet Media Types which you can easily use while development. “Internet Media Type” is the same as a MIME type. MIME types were originally created for…
Read more
SEO is sometimes also called SEO copyrighting because most of the techniques that are used to promote sites in search engines deal with text and images. Videos, images, and infographics are best ways to…
Read more
The Linux tar command stands for tap archive, is not a compressed file and commonly called as a collection (which contains the contents of many files) of a single file. Tar is the…
Read more
cURL is the magical utility that allows developers to download a URL’s content, explore response headers, get stock quotes, confirm our GZip encoding is working, and much more. One more great usage of…
Read more
Netstat is a built in command line tool that provides you with information about TCP connections, network statistics and IP routing table. As it is built in, there is nothing to download. It…
Read more
To check the host the alive or not, we always use PING Command. The “ping” command is built into both Windows and UNIX machines as a universal way of testing network response time and…
Read more
A 404 Page Error or Not Found error is displayed when you go to a page that doesn’t exist within an active website. One of the most common errors you can come across…
Read more
In the early 90’s GNU/Linux systems consisted of little more than a beta – quality Linux kernel and a small collection of software ported from the GNU project. It was a true hacker’s…
Read more
Windows Defender Security Intelligence (WDSI), formerly known as Microsoft Malware Protection Center (MMPC), is committed to helping Microsoft customers. With Windows Defender Security Intelligence (WDSI) you can explore in-depth threat encyclopedia for information…
Read more
Netstat is truly a very overlooked tool for network troubleshooting so I believe that it would be beneficial to post all of the switches and options available with NETSTAT. Netstat displays protocol statistics…
Read more
Headers and methods work together to determine what clients and servers do. This article quickly sketches the purposes of the standard HTTP headers and some headers that are not explicitly defined in the…
Read more
HTTP status codes are classified into 5 broad categories. The status codes provide an easy way for clients to understand the results of their transactions. As methods tell the server what to do,…
Read more
Phishing has emerged as an effective method to steal the personal and confidential data of users. It is an Internet scam that tricks users into divulging their personal and confidential information by making…
Read more
Before a command is executed, its input and output may be redirected using a special notation interpreted by the shell. Redirection allows commands’ file handles to be duplicated, opened, closed, made to refer…
Read more


