
As part of a security audit, evaluation, and “pentesting“, a command execution vulnerability may be discovered (RCE – Remote Command Execution). The listener quickly needs to have a full interactive shell depending on…
Read more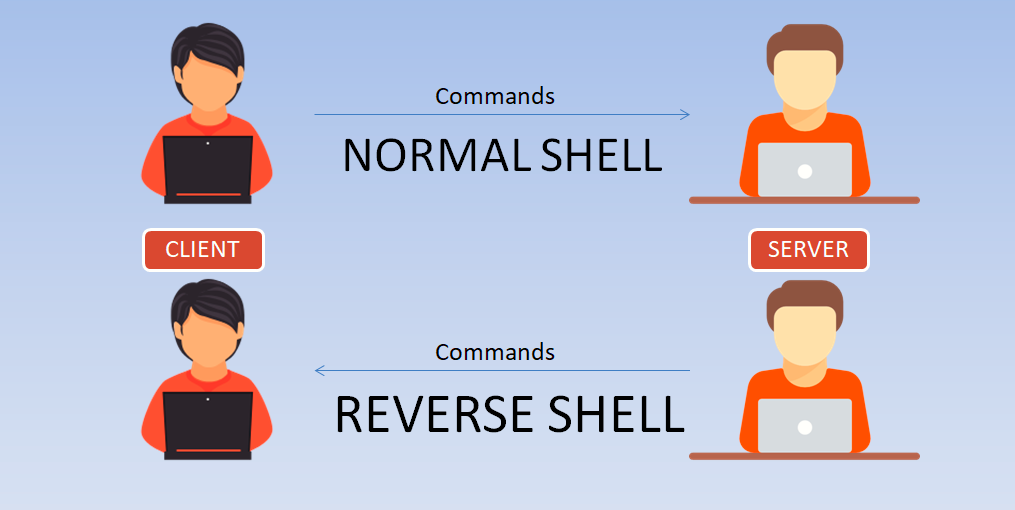
Today we’re are going to show you how to make a reverse shell of any Linux machine. Here in this scenario, we are using two linux based VMs, One is Kali Linux(2017.2) and…
Read more