
Nmap is a free tool that can be used to conduct various sorts of scans on networks. Normally, when people think of Nmap, they assume it’s used to conduct some sort of nefarious network reconnaissance in preparation for an attack. But as with all powerful tools, Nmap can be used for far more than breaking into networks.
One very important aspect of NMAP to remember is that these scans should be ran with Root or Administrator access depending on the type of system you are using. This is required because the scans send raw packets which require privileged system access.
Of the scan types listed below table, only the connect and ftp bounce scans can be ran without privileged access. The last thing to remember is that these scans can only be ran one at a time except if you are running a UDP and TCP scan at the same time.
Now let us take a look at the parameters NMAP uses to perform the different types of system scans. Remember the basic command line format for nmap is:
Syntax: nmap <scan type> <options> <target>
| S.No |
Title |
Command Syntax |
POC (click to enlarge) |
| Target Selection |
| 1 |
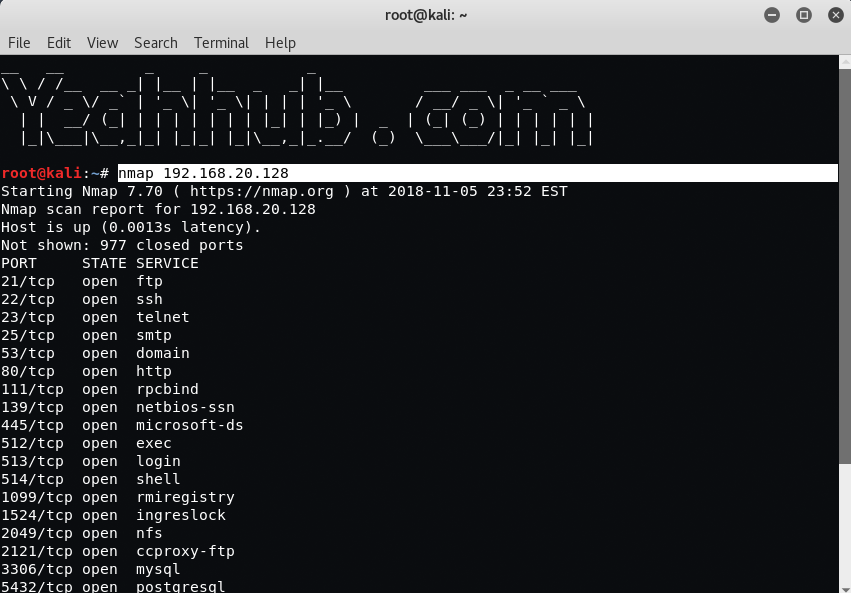
Scan a single IP |
nmap 192.168.20.128 |
 |
| 2 |
Scan a host |
nmap www.example.com |
 |
| 3 |
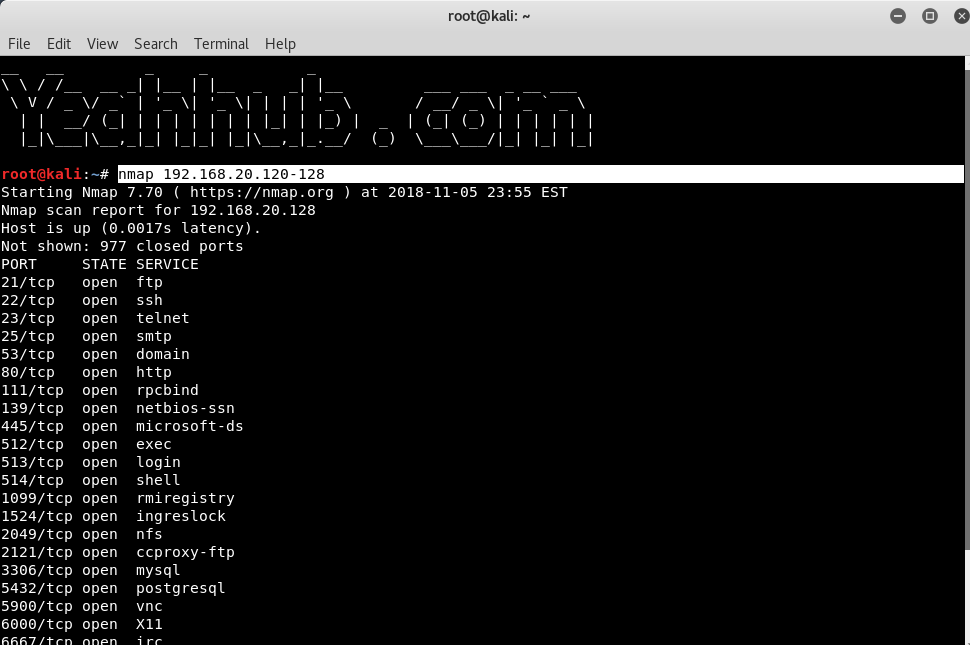
Scan a range of IPs |
nmap 192.168.20.120-128 |
 |
| 4 |
Scan a subnet |
nmap 192.168.20.2/24 |
 |
| 5 |
Scan targets from Text file |
nmap -iL ips.txt |
 |
| Port Selection |
| 6 |
Scan a single port |
nmap -p 22 192.168.20.128 |
 |
| 7 |
Scan a range of ports |
nmap -p 1-100 192.168.20.128 |
 |
| 8 |
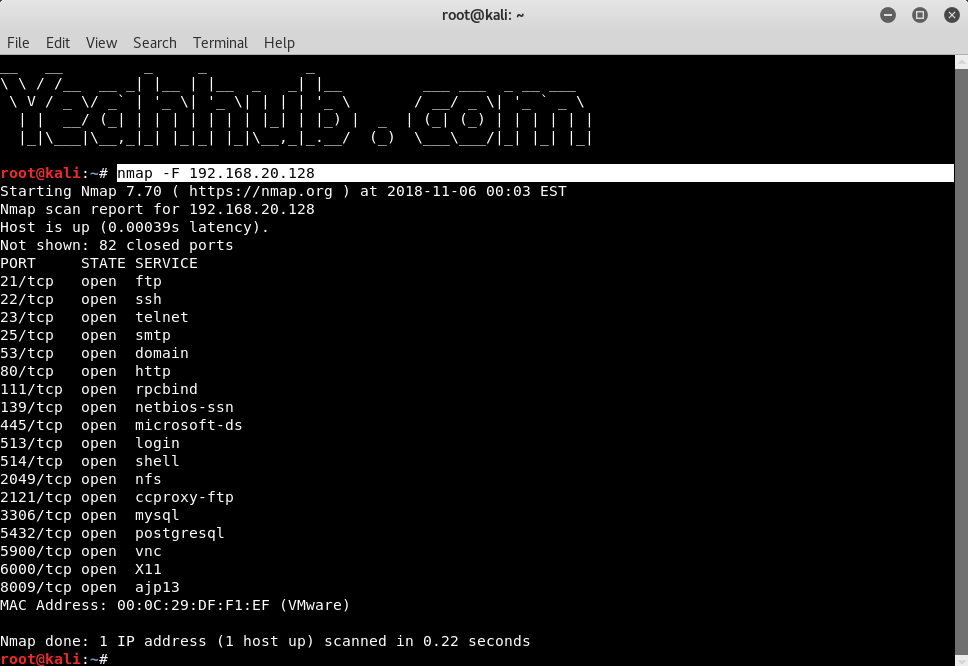
Scan 100 common ports |
nmap -F 192.168.20.128 |
 |
| 9 |
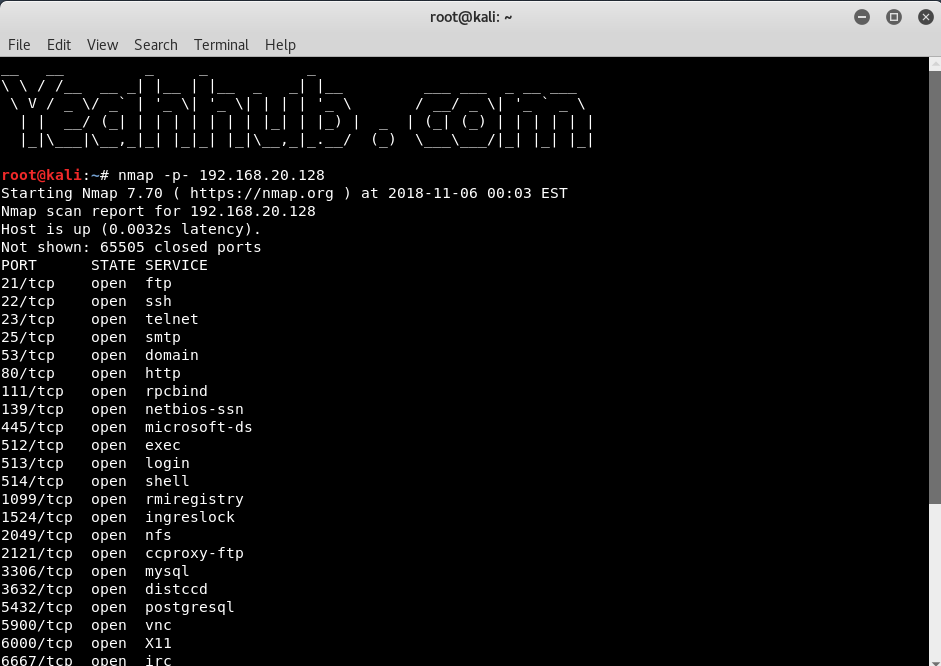
Scan all ports |
nmap -p- 192.168.20.128 |
 |
| 10 |
Specify UDP or TCP scan |
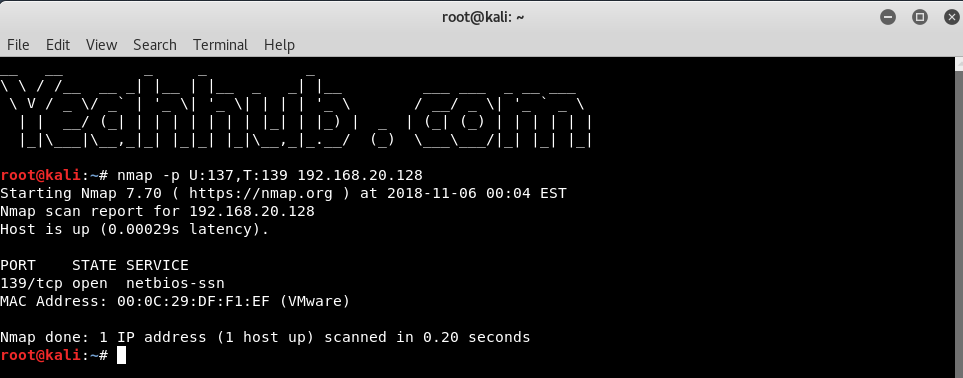
nmap -p U:137,T:139 192.168.20.128 |
 |
| Scan Types |
| 11 |
Scan using TCP connect |
nmap -sT 192.168.20.128 |
 |
| 12 |
Scan using TCP SYN scan |
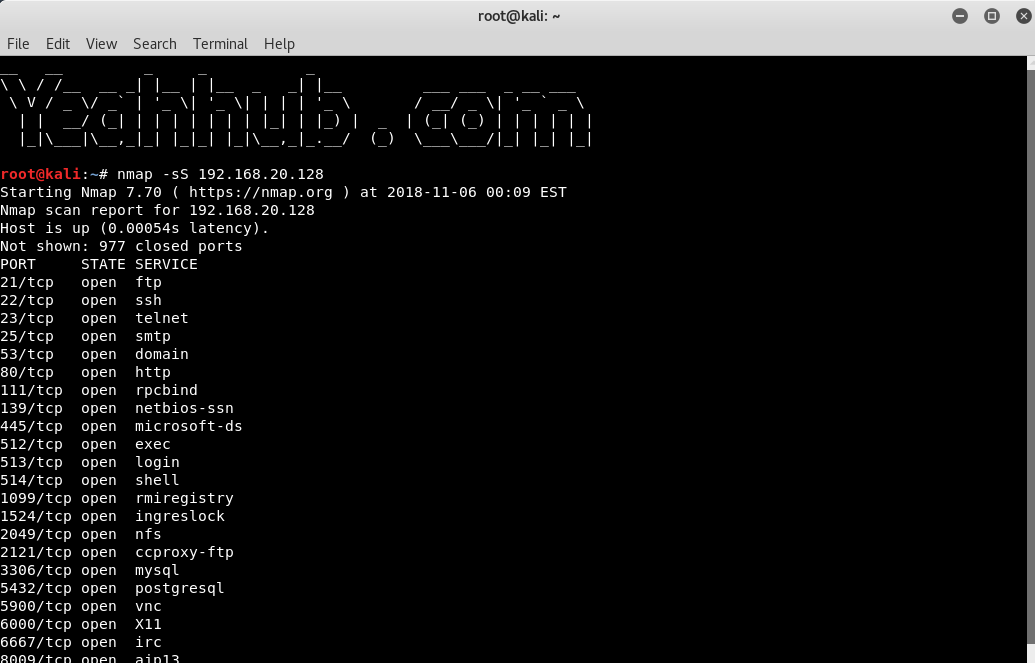
nmap -sS 192.168.20.128 |
 |
| 13 |
Scan UDP ports |
nmap -sU -p 123,161,162 192.168.20.128 |
 |
| 14 |
Scan Selected ports (Ignore Discovery) |
nmap -Pn -F 192.168.20.128 |
 |
| Service and OS Detection |
| 15 |
Detect OS and Services |
nmap -A 192.168.20.128 |
 |
| 16 |
Standard service detection |
nmap -sV 192.168.20.128 |
 |
| 17 |
Aggressive service detection |
nmap -sV –version-intensity 5 192.168.20.128 |
 |
| Output Formats |
| 18 |
Save default output to file |
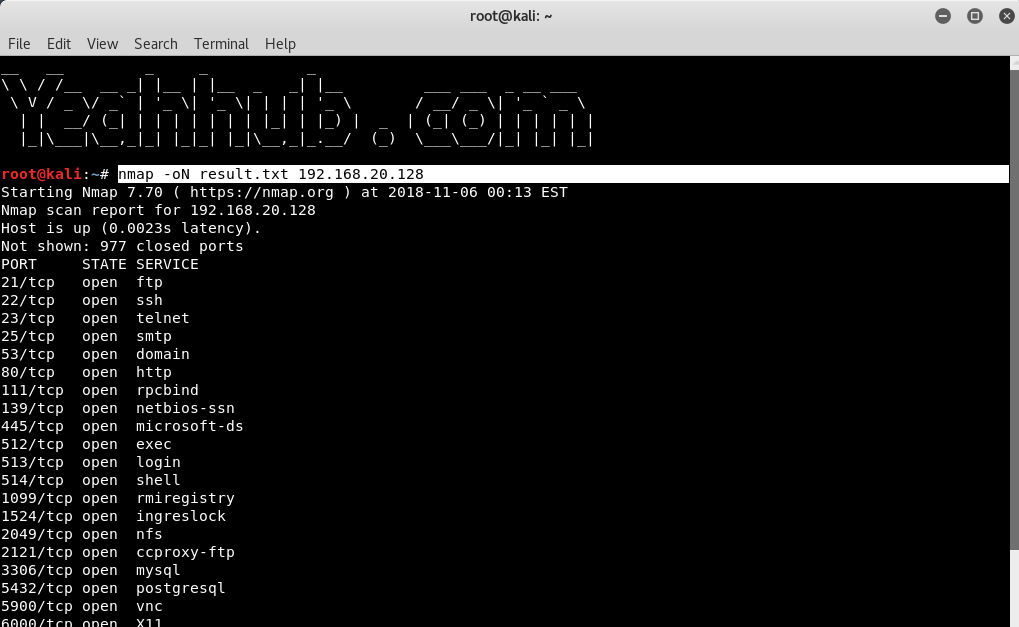
nmap -oN result.txt 192.168.20.128 |
 |
| 19 |
Save results as XML |
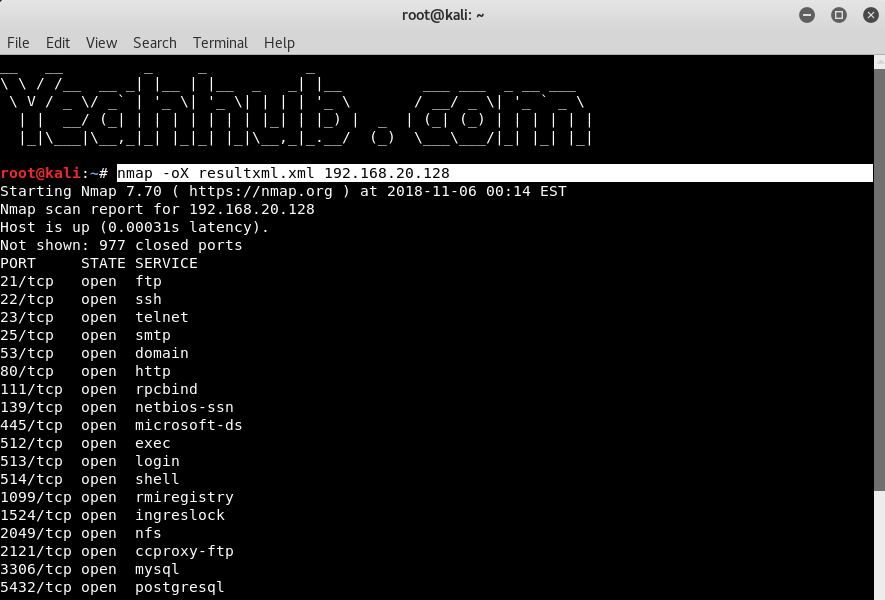
nmap -oX resultxml.xml 192.168.20.128 |
 |
| 20 |
Save formatted results (Grep) |
nmap -oG formattable.txt 192.168.20.128 |
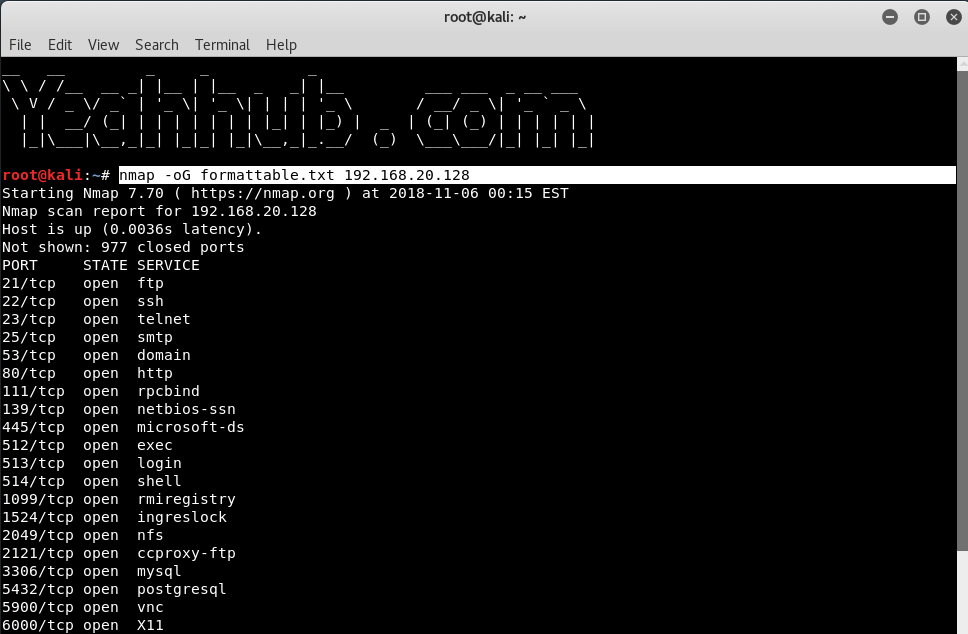 |
| 21 |
Save in all formats |
nmap -oA allformats 192.168.20.128 |
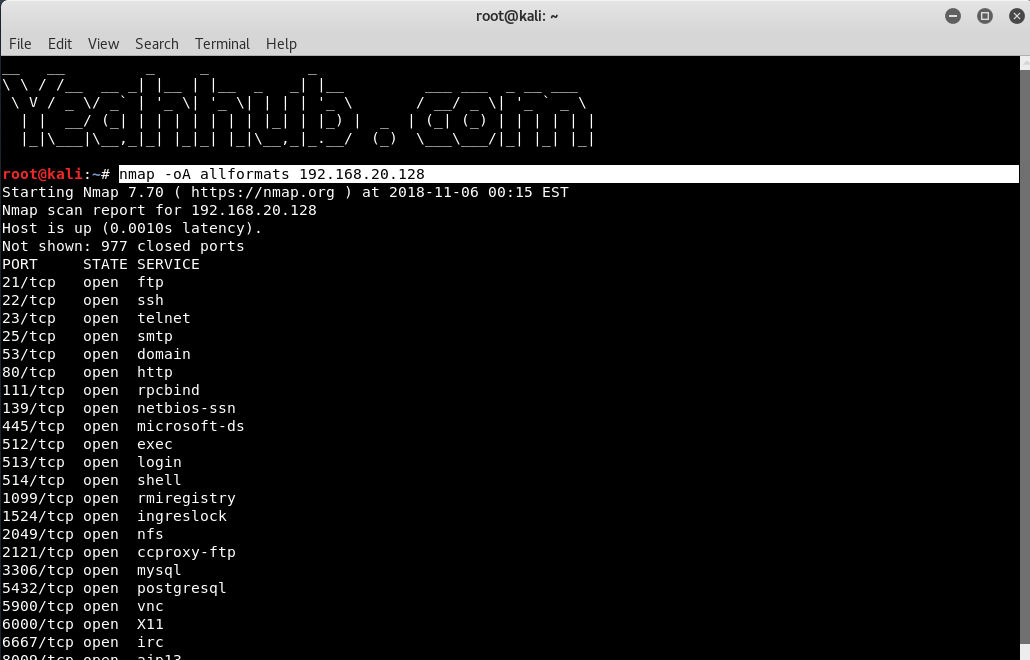 |
| Scripting Engine |
| 22 |
Scan using default safe scripts |
nmap -sV -sC 192.168.20.128 |
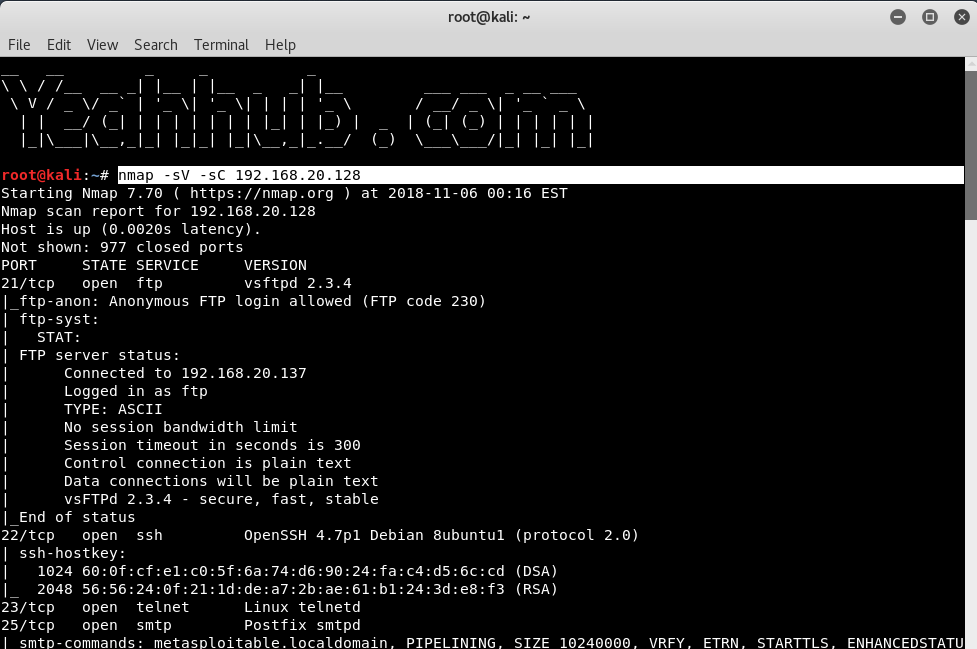 |
| 23 |
Get help for a script |
nmap –script-help=ssl-heartbleed |
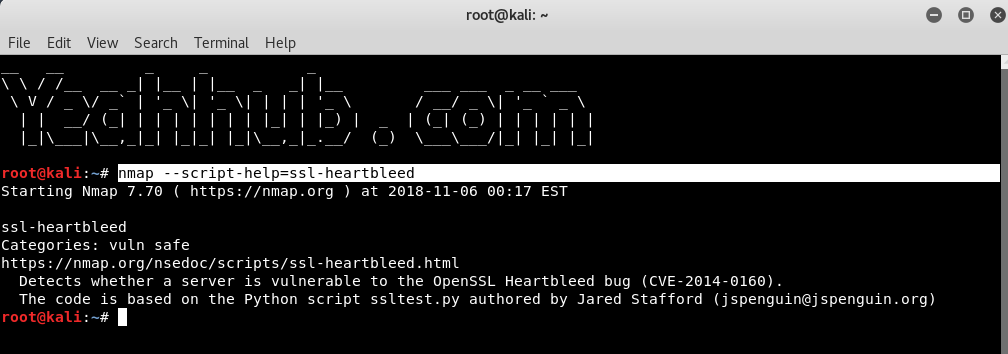 |
| 24 |
Scan using a specific script |
nmap -sV -p 443 -script=ssl-heartbleed 192.168.20.133 |
 |
| 25 |
Update script database |
nmap –script-updatedb |
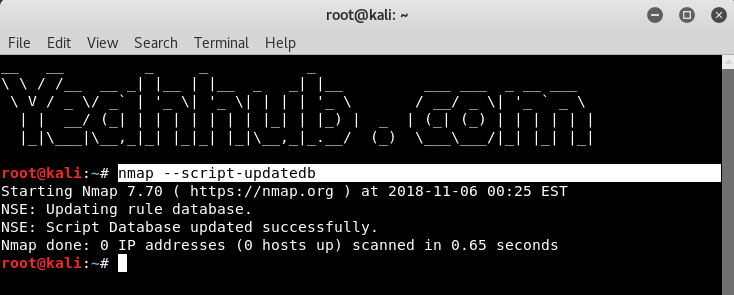 |
| Some Useful NSE Scripts |
| 26 |
Scan for UDP DDOS reflectors |
nmap -sU -A -PN -n -pU:19,53,123,161 -script=ntp-monlist,dns-recursion,snmp-sysdescr 192.168.20.2/24 |
 |
| 27 |
Gather page titles from HTTP Servers |
nmap –script=http-title 192.168.20.128 |
 |
| 28 |
Get HTTP headers of web services |
nmap –script=http-headers 192.168.20.128 |
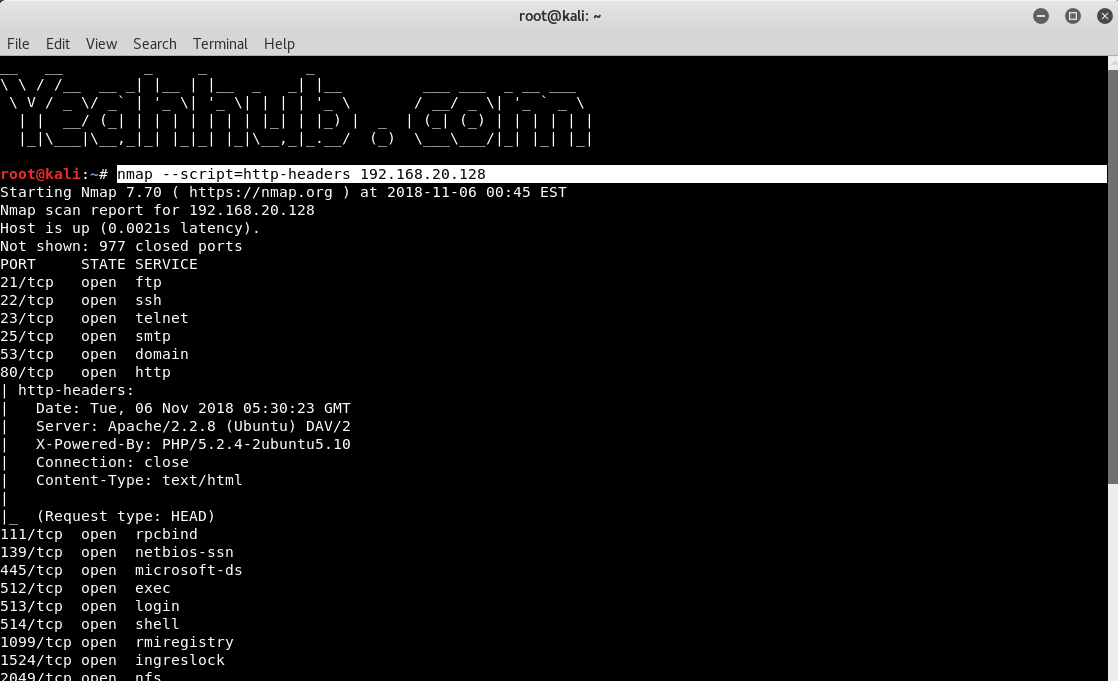 |
| 29 |
Find web apps from known paths |
nmap –script=http-enum 192.168.20.128 |
 |
| 30 |
Find exposed Netbios servers |
nmap -sU –script nbtstat.nse -p 137 192.168.20.128 |
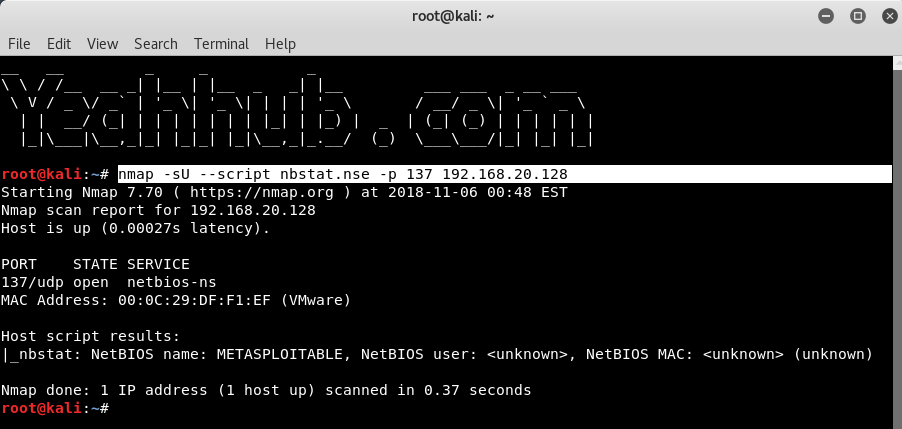 |
The thing to remember is that running different types of scans may produce different results as firewalls may limit the responses allowed from the specific hosts it protects.
More References –







































