CEH v11
INDEX
- Set 1 (Q1 to Q30)
- Set 2 (Q31 to Q60)
- Set 3 (Q61 to Q90)
- Set 4 (Q91 to Q120)
- Set 5 (Q121 to Q150)
- Set 6 (Q151 to Q180)
- Set 7 (Q181 to Q210)
- Set 8 (Q211 to Q240)
- Set 9 (Q241 to Q270)
- Set 10 (Q271 to Q300)
- Set 11 (Q301 to Q330)
- Set 12 (Q331 to Q360)
- Set 13 (Q361 to Q390)
- Set 14 (Q391 to Q420)
- Set 15 (Q421 to Q450)
- Set 16 (Q451 to Q480)
- Set 17 (Q481 to Q510)
- Set 18 (Q511 to Q540)
- Set 19 (Q541 to Q570)
- Set 20 (Q571 to Q600)
- Set 21 (Q601 to Q630)
- Set 22 (Q631 to Q660)
- Set 23 (Q661 to Q690)
- Set 24 (Q691 to Q720)
Q181 - Which of the following types of jailbreaking allows user-level access but does not allow iboot-level access?
- Bootrom Exploit
- iBoot Exploit
- Sandbox Exploit
- Userland Exploit
Answer: D
Q182 - Jack was attempting to fingerprint all machines in the network using the following Nmap syntax:
invictus@victim_server:~$ nmap -T4 -0 10.10.0.0/24
TCP/IP fingerprinting (for OS scan) xxxxxxx xxxxxx xxxxxxxxx. QUITTING!
Obviously, it is not going through. What is the issue here?
- OS Scan requires root privileges
- The nmap syntax is wrong.
- The outgoing TCP/IP fingerprinting is blocked by the host firewall
- This is a common behavior for a corrupted nmap application
Answer: A
Q183 - What did the following commands determine?
- That the Joe account has a SID of 500
- These commands demonstrate that the guest account has NOT been disabled
- These commands demonstrate that the guest account has been disabled
- That the true administrator is Joe
- Issued alone, these commands prove nothing
Answer: D
Q184 - Todd has been asked by the security officer to purchase a counter-based authentication system. Which of the following best describes this type of system?
- A biometric system that bases authentication decisions on behavioral attributes.
- A biometric system that bases authentication decisions on physical attributes.
- An authentication system that creates one-time passwords that are encrypted with secret keys.
- An authentication system that uses passphrases that are converted into virtual passwords.
Answer: C
Q185 - WPA2 uses AES for wireless data encryption at which of the following encryption levels?
- 64 bit and CCMP
- 128 bit and CRC
- 128 bit and CCMP
- 128 bit and TKIP
Answer: C
Q186 - While examining audit logs, you discover that people are able to telnet into the SMTP server on port 25. You would like to block this, though you do not see any evidence of an attack or other wrong doing. However, you are concerned about affecting the normal functionality of the email server. From the following options choose how best you can achieve this objective?
- Block port 25 at the firewall.
- Shut off the SMTP service on the server.
- Force all connections to use a username and password.
- Switch from Windows Exchange to UNIX Sendmail.
- None of the above.
Answer: E
Q187 - You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c
What is the hexadecimal value of NOP instruction?
- 0x60
- 0x80
- 0x70
- 0x90
Answer: D
Q188 - A virus that attempts to install itself inside the file it is infecting is called?
- Tunneling virus
- Cavity virus
- Polymorphic virus
- Stealth virus
Answer: B
Q189 - Which NMAP command combination would let a tester scan every TCP port from a class C network that is blocking ICMP with fingerprinting and service detection?
- NMAP -PN -A -O -sS 192.168.2.0/24
- NMAP -P0 -A -O -p1-65535 192.168.0/24
- NMAP -P0 -A -sT -p0-65535 192.168.0/16
- NMAP -PN -O -sS -p 1-1024 192.168.0/8
Answer: B
Q190 - Port scanning can be used as part of a technical assessment to determine network vulnerabilities. The TCP XMAS scan is used to identify listening ports on the targeted system. If a scanned port is open, what happens?
- The port will ignore the packets.
- The port will send an RST.
- The port will send an ACK.
- The port will send a SYN.
Answer: A
Q191 - Which type of security feature stops vehicles from crashing through the doors of a building?
- Turnstile
- Bollards
- Mantrap
- Receptionist
Answer: B
Q192 - Which of the following programs is usually targeted at Microsoft Office products?
- Polymorphic virus
- Multipart virus
- Macro virus
- Stealth virus
Answer: C
Q193 - An engineer is learning to write exploits in C++ and is using the exploit tool Backtrack. The engineer wants to compile the newest C++ exploit and name it calc.exe. Which command would the engineer use to accomplish this?
- g++ hackersExploit.cpp -o calc.exe
- g++ hackersExploit.py -o calc.exe
- g++ -i hackersExploit.pl -o calc.exe
- g++ --compile -i hackersExploit.cpp -o calc.exe
Answer: A
Q194 - An Intrusion Detection System (IDS) has alerted the network administrator to a possibly malicious sequence of packets sent to a Web server in the network's external DMZ. The packet traffic was captured by the IDS and saved to a PCAP file. What type of network tool can be used to determine if these packets are genuinely malicious or simply a false positive?
- Protocol analyzer
- Intrusion Prevention System (IPS)
- Network sniffer
- Vulnerability scanner
Answer: A
Q195 - A server has been infected by a certain type of Trojan. The hacker intended to utilize it to send and host junk mails. What type of Trojan did the hacker use?
- Turtle Trojans
- Ransomware Trojans
- Botnet Trojan
- Banking Trojans
Answer: C
Q196 - The security administrator of ABC needs to permit Internet traffic in the host 10.0.0.2 and UDP traffic in the host 10.0.0.3. Also he needs to permit all FTP traffic to the rest of the network and deny all other traffic. After he applied his ACL configuration in the router nobody can access to the ftp and the permitted hosts cannot access to the Internet. According to the next configuration what is happening in the network?
- The ACL 110 needs to be changed to port 80
- The ACL for FTP must be before the ACL 110
- The first ACL is denying all TCP traffic and the other ACLs are being ignored by the router
- The ACL 104 needs to be first because is UDP
Answer: C
Q197 - What results will the following command yield: 'NMAP -sS -O -p 123-153 192.168.100.3'?
- A stealth scan, opening port 123 and 153
- A stealth scan, checking open ports 123 to 153
- A stealth scan, checking all open ports excluding ports 123 to 153
- A stealth scan, determine operating system, and scanning ports 123 to 153
Answer: D
Q198 - What does a type 3 code 13 represent? (Choose two.)
- Echo request
- Destination unreachable
- Network unreachable
- Administratively prohibited
- Port unreachable
- Time exceeded
Answer: B and D
Q199 - Which access control mechanism allows for multiple systems to use a central authentication server (CAS) that permits users to authenticate once and gain access to multiple systems?
- Role Based Access Control (RBAC)
- Discretionary Access Control (DAC)
- Windows authentication
- Single sign-on
Answer: D
Q200 - A hacker is attempting to see which ports have been left open on a network. Which NMAP switch would the hacker use?
- -sO
- -sP
- -sS
- -sU
Answer: A
Q201 - The following is a sample of output from a penetration tester's machine targeting a machine with the IP address of 192.168.1.106: 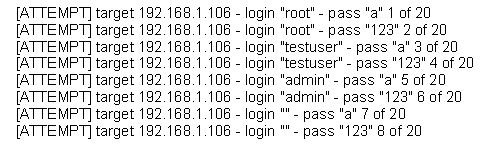
What is most likely taking place?
- Ping sweep of the 192.168.1.106 network
- Remote service brute force attempt
- Port scan of 192.168.1.106
- Denial of service attack on 192.168.1.106
Answer: B
Q202 - Company XYZ has asked you to assess the security of their perimeter email gateway. From your office in New York, you craft a specially formatted email message and send it across the Internet to an employee of Company XYZ. The employee of Company XYZ is aware of your test. Your email message looks like this:
From: jim_miller@companyxyz.com
To: michelle_saunders@companyxyz.com
Subject: Test message
Date: 4/3/2017 14:37
The employee of Company XYZ receives your email message. This proves that Company XYZ's email gateway doesn't prevent what?
- Email Phishing
- Email Masquerading
- Email Spoofing
- Email Harvesting
Answer: C
Q203 - Which of the following LM hashes represent a password of less than 8 characters? (Choose two.)
- BA810DBA98995F1817306D272A9441BB
- 44EFCE164AB921CQAAD3B435B51404EE
- 0182BD0BD4444BF836077A718CCDF409
- CEC52EB9C8E3455DC2265B23734E0DAC
- B757BF5C0D87772FAAD3B435B51404EE
- E52CAC67419A9A224A3B108F3FA6CB6D
Answer: B and E
Q204 - A software tester is randomly generating invalid inputs in an attempt to crash the program. Which of the following is a software testing technique used to determine if a software program properly handles a wide range of invalid input?
- Mutating
- Randomizing
- Fuzzing
- Bounding
Answer: C
Q205 - SOAP services use which technology to format information?
- SATA
- PCI
- XML
- ISDN
Answer: C
Q206 - Which type of sniffing technique is generally referred as MiTM attack?
- Password Sniffing
- ARP Poisoning
- Mac Flooding
- DHCP Sniffing
Answer: B
Q207 - When security and confidentiality of data within the same LAN is of utmost priority, which IPSec mode should you implement?
- AH Tunnel mode
- AH promiscuous
- ESP transport mode
- ESP confidential
Answer: C
Q208 - You're doing an internal security audit and you want to find out what ports are open on all the servers. What is the best way to find out?
- Scan servers with Nmap
- Physically go to each server
- Scan servers with MBSA
- Telent to every port on each server
Answer: A
Q209 - Session splicing is an IDS evasion technique in which an attacker delivers data in multiple, smallsized packets to the target computer, making it very difficult for an IDS to detect the attack signatures. Which tool can be used to perform session splicing attacks?
- Whisker
- tcpsplice
- Burp
- Hydra
Answer: A
Q210 - A penetration tester was hired to perform a penetration test for a bank. The tester began searching for IP ranges owned by the bank, performing lookups on the bank's DNS servers, reading news articles online about the bank, watching what times the bank employees come into work and leave from work, searching the bank's job postings (paying special attention to IT related jobs), and visiting the local dumpster for the bank's corporate office. What phase of the penetration test is the tester currently in?
- Information reporting
- Vulnerability assessment
- Active information gathering
- Passive information gathering
Answer: D



















